Abstract
TL;DR: We investigate how skip connections in deep neural networks affect vulnerability to model inversion attacks and propose MI-resilient architectures based on this understanding.
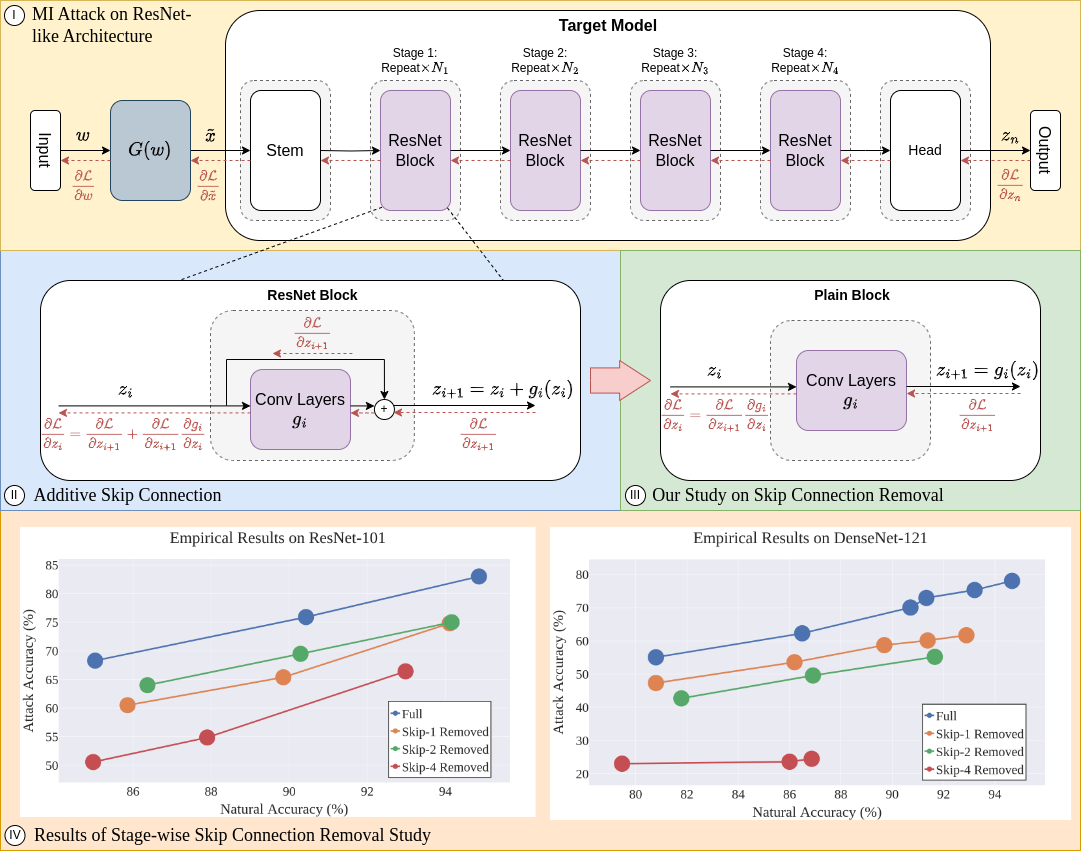
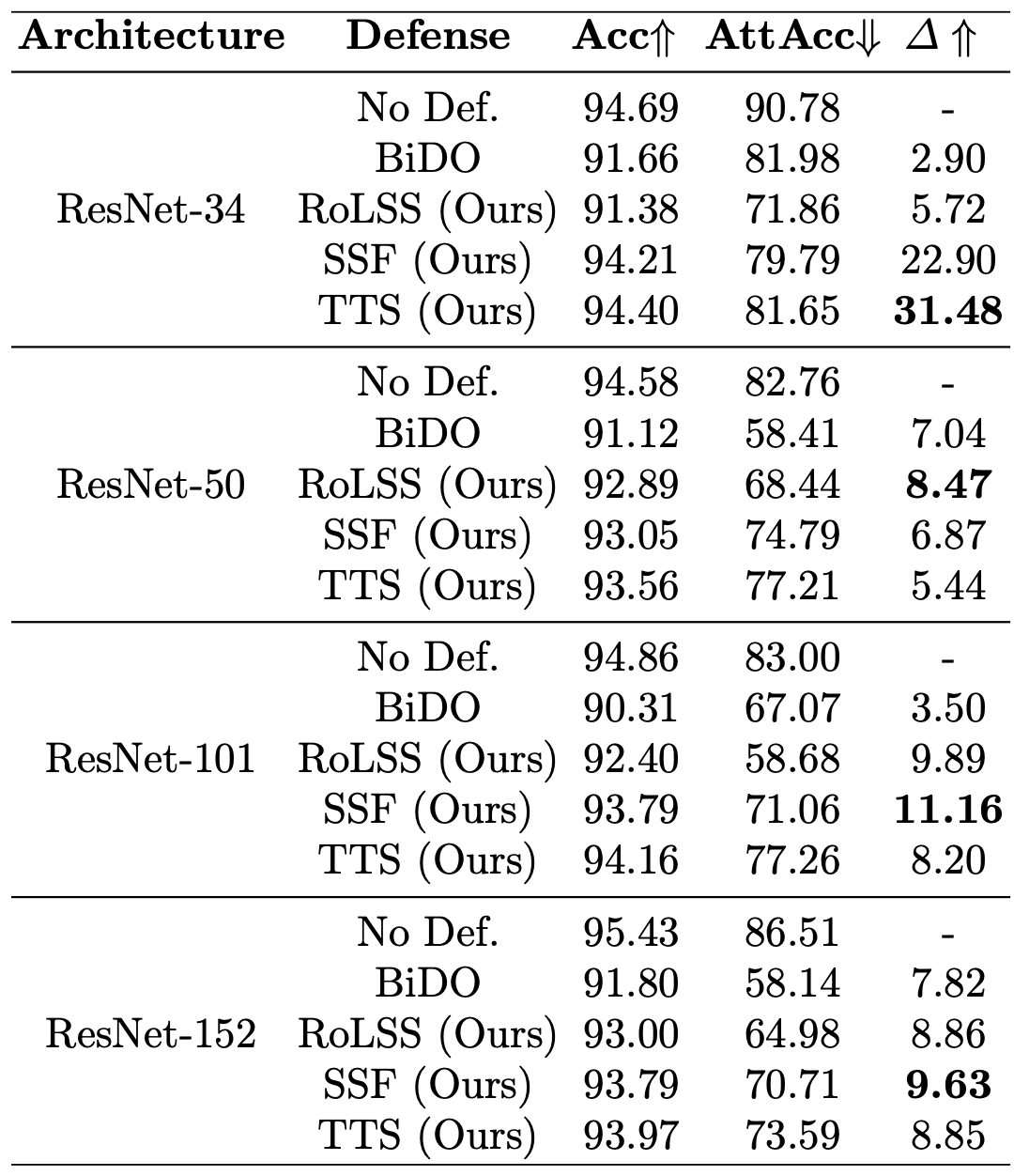
Skip connections are fundamental architecture designs for modern deep neural networks (DNNs) such as CNNs and ViTs. While they help improve model performance significantly, we identify a vulnerability associated with skip connections to Model Inversion (MI) attacks, a type of privacy attack that aims to reconstruct private training data through abusive exploitation of a model. In this paper, as a pioneer work to understand how DNN architectures affect MI, we study the impact of skip connections on MI. We make the following discoveries: 1) Skip connections reinforce MI attacks and compromise data privacy. 2) Skip connections in the last stage are the most critical to attack. 3) RepVGG, an approach to remove skip connections in the inference-time architectures, could not mitigate the vulnerability to MI attacks. 4) Based on our findings, we propose MI-resilient architecture designs for the first time. Without bells and whistles, we show in extensive experiments that our MI-resilient architectures can outperform state-of-the-art (SOTA) defense methods in MI robustness. Furthermore, our MI-resilient architectures are complementary to existing MI defense methods.
BibTeX
@article{koh2024vulnerability,
title={On the vulnerability of skip connections to model inversion attacks},
author={Koh, Jun Hao and Ho, Sy-Tuyen and Nguyen, Ngoc-Bao and Cheung, Ngai-man},
journal={arXiv preprint arXiv:2409.01696},
year={2024}
}